Nikos Mavrogiannopoulos
on 16 December 2021
How we designed Ubuntu Pro for Confidential Computing on Azure
Not all data is destined to be public. Moving workloads that handle secret or private data from an on-premise setup to a public cloud introduces a new attack surface with different risks. As the public cloud environment shares its hardware infrastructure, a flaw in the clouds’ isolation mechanisms can be detrimental to the protection of sensitive data. The major public cloud environments tackle this by building their security following a defense-in-depth approach. Confidential Computing is an additional layer of security in this environment to keep data private even when a flaw is found in the other defense mechanisms. While the field of Confidential Computing has attracted a lot of scientific and academic interest, today’s practical solutions involve isolated enclaves from the main system. In this post, we examine how isolation is achieved with Ubuntu Pro confidential VMs on the Microsoft Azure platform.
While there are multiple solutions involving secure enclaves today, they often require specialized software to take advantage of them. On the other hand, the Microsoft Azure confidential VMs only require changes to the operating system, while existing workloads run without any change on a familiar environment like Ubuntu. That makes it one of the most promising technologies in Confidential Computing.
Although the technology is still in a public preview phase, Ubuntu is one of the first operating systems to support it. You can join this preview phase today and validate your workloads against Ubuntu. For more information, see this quick start guide from Microsoft.
How can workloads be kept private on the cloud?
Confidential Computing is not new; science and academia have worked towards that goal for several decades already with homomorphic encryption. Homomorphic encryption’s goal is to allow untrusted parties to operate on data without accessing that data. It has taken many trees worth of paper to report on work and results for homomorphic encryption, but while there are quite a few homomorphic encryption schemes today, they are rarely used in practice.
While the pursuit of homomorphic encryption for technology that enables us to completely hide our data from public cloud providers may well be successful in the future, today Confidential Computing improves the security on the public clouds without targeting an all-or-nothing approach. Confidential Computing reduces the attack surface on a cloud environment with a defense-in-depth architecture. This is achieved by taking advantage of security technologies available on CPUs, such as the AMD SEV family of technologies, TPMs, and the security features on an operating system such as Ubuntu. Let’s now see how these defenses are established on the Azure environment with Ubuntu.
How does Ubuntu enable Confidential Computing on Microsoft Azure?
Run-time VM memory encryption
The Microsoft Azure AMD-based confidential VMs are based on the AMD SEV family of technologies (SEV, SEV-ES, SEV-SNP). This ensures that VMs are run in a special environment where their memory and CPU registers are encrypted with an AES key, ensuring that no other VM or the host administrator can peek at the processed data. It works as shown in the following simplified diagram.

When the CPU is operating in the guest VM, it will always encrypt the memory locations it writes, and decrypt when reading. Different VMs have access to different areas that are tagged for them. That means that, in the event of a hypervisor breach, a VM cannot retrieve memory from a different VM but can only see the encrypted version of it.

This model enables private VMs on the public cloud that can handle confidential workloads. At the same time, this is only a part of the security story on the cloud. Although the run-time memory encryption is a very important piece of the whole story, workloads that run on the cloud are loaded from a hard disk, typically located in the cloud’s infrastructure.
VM encryption at rest
That brings us to VM disk encryption. The security of data at rest is provided by the Ubuntu operating system. With its support for full disk encryption, Ubuntu ensures that all the data written at disk are encrypted and decrypted with AES, as well as that each boot step is validated using the UEFI secure boot. The key for the disk encryption is stored in the virtual disk in an encrypted form. This encrypted key blob can only be decrypted by the virtual Trusted Platform Module (vTPM) of Azure associated with the VM instance.

VM encryption during boot time and run-time
During boot time, Ubuntu’s early boot environment (initrd) loads the key blob into the vTPM, and then, in turn, loads the kernel and attests that it is in a specific state before the vTPM makes the VM decryption keys accessible. The decryption keys can only be read by this VM. A simplified view of this process is shown in the following diagrams.
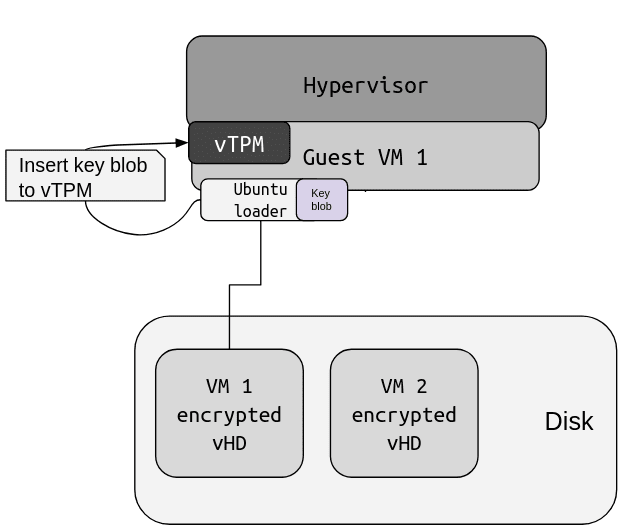 | 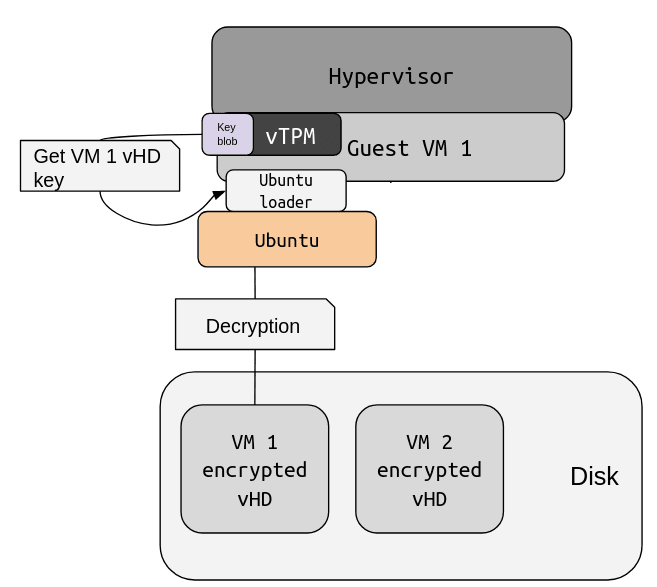 |
The vTPM operates within the Guest VM address space, so it is protected by the run-time memory encryption of the CPU, and is also encrypted at rest.
VM during run-time
During run-time, the system has isolated its resources from other tenants by taking advantage of the AMD CPU features, Ubuntu security features, and the vTPM’s ability to separate secrets. As a result, the security surface is more compact, offering VM isolation by protecting from attacks on the hypervisor. The following diagram demonstrates the isolation of memory and disk using Ubuntu.

What does this mean for me?
By moving to the public cloud, an organization trusts its public cloud infrastructure, in addition to its own IT department to keep its data secure. With Confidential Computing you can additionally benefit from the security mechanisms built-in the hypervisor for VM memory and disk isolation, and take advantage of encryption as an isolation mechanism. Encryption as a memory isolation mechanism is enforced by the CPU, while encryption as a disk isolation mechanism is enforced by Ubuntu and the vTPM. That builds into the existing protections of the hypervisor, raising an additional line on the defense-in-depth architecture.
At the same time, the protection offered by Confidential Computing on Azure depends on specially enabled VM images, but comes with no changes to the workloads. Whether it is a database like postgres being run on Ubuntu, or a kubernetes cluster, their administration and operation works the same way as previously with the standard “non-confidential” VMs. Ubuntu absorbs the complexity of the implementation, giving a frictionless transition to the new confidential environment.
How can I use Ubuntu Confidential Computing on Azure?
An Ubuntu image tailored for Confidential Computing is available on Microsoft Azure (currently in the preview phase) to enable testing the migration to the platform. For production workloads, we are making available Ubuntu Pro images tailored for Confidential Computing. To try Ubuntu with Confidential Computing on Azure today, see this quick start guide from Microsoft.


